X-Proxy 6.2.0.4
Did you know your IP address is exposed every time you visit a website? Identity thieves may use your IP address to monitor your web activity and intercept your private information.
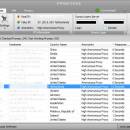
X-Proxy is designed to avoid these problems, as it helps you hide your IP address in order to surf the Web anonymously. With X-Proxy can prevent others from seeing your true IP when browsing the Internet. ...
| Author | Sauces Software |
| License | Freeware |
| Price | FREE |
| Released | 2019-12-24 |
| Downloads | 1682 |
| Filesize | 522 kB |
| Requirements | Microsoft .NET Framework 4 (x86 and x64), Windows Installer 4.5 |
| Installation | Instal And Uninstall |
| Keywords | hide IP, IP address changer, change IP, hide, changer, change |
| Users' rating (30 rating) |
Using X-Proxy Free Download crack, warez, password, serial numbers, torrent, keygen, registration codes,
key generators is illegal and your business could subject you to lawsuits and leave your operating systems without patches.
We do not host any torrent files or links of X-Proxy on rapidshare.com, depositfiles.com, megaupload.com etc.
All X-Proxy download links are direct X-Proxy full download from publisher site or their selected mirrors.
Avoid: intrusion oem software, old version, warez, serial, torrent, X-Proxy keygen, crack.
Consider: X-Proxy full version, intrusion full download, premium download, licensed copy.