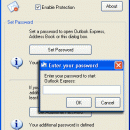
Outlook Express Security 2.397
Use Outlook Express Security to control access to Outlook Express and its databases. When it ... Express becomes locked and no third-party programs can access its message base files and the address book. ... start Outlook Express, open the address book or access the files, a password will be asked to allow access. If an invalid password is entered, Outlook Express or Address Book will not be opened. ...
| Author | IM-Soft |
| License | Free To Try |
| Price | $29.00 |
| Released | 2015-04-16 |
| Downloads | 847 |
| Filesize | 717 kB |
| Requirements | n/a |
| Installation | Install and Uninstall |
| Keywords | access, files, book, address, password, security, allow, message, base, control, try, third, start, result, programs, party, open, locked, databases, data, becomes, asked, active, outlook, express |
| Users' rating (8 rating) |
Using Outlook Express Security Free Download crack, warez, password, serial numbers, torrent, keygen, registration codes,
key generators is illegal and your business could subject you to lawsuits and leave your operating systems without patches.
We do not host any torrent files or links of Outlook Express Security on rapidshare.com, depositfiles.com, megaupload.com etc.
All Outlook Express Security download links are direct Outlook Express Security full download from publisher site or their selected mirrors.
Avoid: access oem software, old version, warez, serial, torrent, Outlook Express Security keygen, crack.
Consider: Outlook Express Security full version, access full download, premium download, licensed copy.