Vov Log Analyzer 1.5
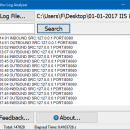
In computing, a log file is a file that records either events that occur in an operating system or other software runs, or messages between different users of a communication software. Logging is the act of keeping a log. In the simplest case, messages are written to a single logfile. Many operating systems, software frameworks, and programs include a logging system. Vov Log Analyzer is a tool to analyze big log files. ...
| Author | VOVSOFT |
| License | Free To Try |
| Price | $9.99 |
| Released | 2018-12-17 |
| Downloads | 97 |
| Filesize | 1.60 MB |
| Requirements | Windows XP or later. |
| Installation | Install and Uninstall |
| Keywords | log, logs, logger, logging, analysis, analyze, analyze |
| Users' rating (13 rating) |
Using Vov Log Analyzer Free Download crack, warez, password, serial numbers, torrent, keygen, registration codes,
key generators is illegal and your business could subject you to lawsuits and leave your operating systems without patches.
We do not host any torrent files or links of Vov Log Analyzer on rapidshare.com, depositfiles.com, megaupload.com etc.
All Vov Log Analyzer download links are direct Vov Log Analyzer full download from publisher site or their selected mirrors.
Avoid: computing oem software, old version, warez, serial, torrent, Vov Log Analyzer keygen, crack.
Consider: Vov Log Analyzer full version, computing full download, premium download, licensed copy.