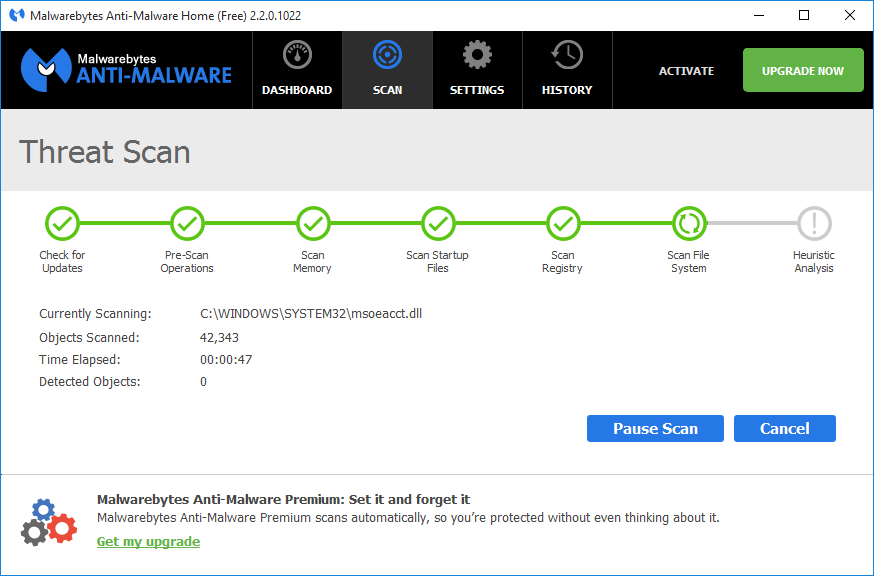
Malwarebytes Chameleon 3.1.33.0
Protects and guards Malwarebytes Anti-Malware against malware's attempts to disable it. Malwarebytes Chameleon technologies gets Malwarebytes Anti-Malware installed and running when blocked by malicious programs. It is a command-line utility, yet this does not imply it should only be used by tech-savvy ones as no user input is required once the tool is launched, as all the actions are initiated automatically. ...
| Author | Malwarebytes |
| License | Freeware |
| Price | FREE |
| Released | 2016-05-24 |
| Downloads | 109 |
| Filesize | 6.10 MB |
| Requirements | |
| Installation | Instal And Uninstall |
| Keywords | Malware Removal, Detect Malware, Launch Anti-Malware, Anti-malware, Detection, Removal, Scanner |
| Users' rating (7 rating) |
Using Malwarebytes Chameleon Free Download crack, warez, password, serial numbers, torrent, keygen, registration codes,
key generators is illegal and your business could subject you to lawsuits and leave your operating systems without patches.
We do not host any torrent files or links of Malwarebytes Chameleon on rapidshare.com, depositfiles.com, megaupload.com etc.
All Malwarebytes Chameleon download links are direct Malwarebytes Chameleon full download from publisher site or their selected mirrors.
Avoid: detected oem software, old version, warez, serial, torrent, Malwarebytes Chameleon keygen, crack.
Consider: Malwarebytes Chameleon full version, detected full download, premium download, licensed copy.