- Software
- - Network & Internet
- - Other
- - CMUD
CMUD 3.34
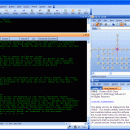
CMUD allows you to connect to and play hundreds of MUD Games on the Internet, and provides you many useful tools, such as aliases, actions, macros, keys, buttons, scripts, maps, databases, etc, to make your MUD player's life easier and more profitable. CMUD is a second-generation MUD client created by the authors of zMUD (Zugg's MUD Client). CMUD is mostly compatible with zMUD, but has been redesigned for improved stability and expandibility. ...
| Author | Zugg Software |
| License | Trialware |
| Price | $34.95 |
| Released | 2019-07-09 |
| Downloads | 609 |
| Filesize | 11.00 MB |
| Requirements | |
| Installation | Instal And Uninstall |
| Keywords | MUD client, online environment, MUD game, client, script, map |
| Users' rating (23 rating) |
Using CMUD Free Download crack, warez, password, serial numbers, torrent, keygen, registration codes,
key generators is illegal and your business could subject you to lawsuits and leave your operating systems without patches.
We do not host any torrent files or links of CMUD on rapidshare.com, depositfiles.com, megaupload.com etc.
All CMUD download links are direct CMUD full download from publisher site or their selected mirrors.
Avoid: from file name oem software, old version, warez, serial, torrent, CMUD keygen, crack.
Consider: CMUD full version, from file name full download, premium download, licensed copy.