WildBlue Bandwidth Monitor 0.1.3.3
... a utility for WildBlue and Exede Internet customers. Log and graph your bandwidth usage with this simple utility.
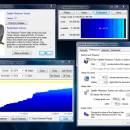
The WildBlue Bandwidth Monitor automatically grabs and stores your current bandwidth usage every hour, showing only a small WildBlue logo in your system tray. When you open the program, you'll see two simple graphs displaying your current download. ...
| Author | RealityRipple |
| License | Freeware |
| Price | FREE |
| Released | 2012-07-31 |
| Downloads | 226 |
| Filesize | 901 kB |
| Requirements | |
| Installation | Instal And Uninstall |
| Keywords | bandwidth usage, monitor bandwidth, track bandwidth, bandwidth, usage, WildBlue |
| Users' rating (8 rating) |
Using WildBlue Bandwidth Monitor Free Download crack, warez, password, serial numbers, torrent, keygen, registration codes,
key generators is illegal and your business could subject you to lawsuits and leave your operating systems without patches.
We do not host any torrent files or links of WildBlue Bandwidth Monitor on rapidshare.com, depositfiles.com, megaupload.com etc.
All WildBlue Bandwidth Monitor download links are direct WildBlue Bandwidth Monitor full download from publisher site or their selected mirrors.
Avoid: log in oem software, old version, warez, serial, torrent, WildBlue Bandwidth Monitor keygen, crack.
Consider: WildBlue Bandwidth Monitor full version, log in full download, premium download, licensed copy.