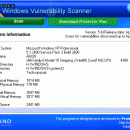
Free Windows Vulnerability Scanner 5.4
Protector Plus -Free Windows Vulnerability Scanner is compatible with Windows 7 ,Windows Vista, Windows XP, Windows Server 2003, Windows Server 2008. Once the Scan is completed, It lists the Vulnerabilities detected, their risk level and the download location of the patch. You are advised to download the latest version of Protector Plus, you can click on Download Protector Plus 2014 button on the scanner to download the same. ...
| Author | Proland Software |
| License | Freeware |
| Price | FREE |
| Released | 2015-04-19 |
| Downloads | 443 |
| Filesize | 1.47 MB |
| Requirements | 450 Mhz CPU, 256 MB RAM, 250 MB Free Disk Space |
| Installation | Install Only |
| Keywords | Free, Vulnerability Scanner, Computer Protection, Anti-virus, utility, Scanning tool, Threat |
| Users' rating (11 rating) |
Using Free Windows Vulnerability Scanner Free Download crack, warez, password, serial numbers, torrent, keygen, registration codes,
key generators is illegal and your business could subject you to lawsuits and leave your operating systems without patches.
We do not host any torrent files or links of Free Windows Vulnerability Scanner on rapidshare.com, depositfiles.com, megaupload.com etc.
All Free Windows Vulnerability Scanner download links are direct Free Windows Vulnerability Scanner full download from publisher site or their selected mirrors.
Avoid: log on oem software, old version, warez, serial, torrent, Free Windows Vulnerability Scanner keygen, crack.
Consider: Free Windows Vulnerability Scanner full version, log on full download, premium download, licensed copy.