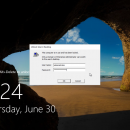
WinUnlock 2.0
... to unlock and access a locked workstation and user desktop. to perform necessary audits, software installations, and provide technical support - all with logged activity so that the balance between convenience and security can be maintained. Desktops will re-lock after 2 minutes of inactivity and return to the Winlogon Desktop (Ctrl+Alt+Delete screen). Idle sessions can be disconnected to free resources. ...
| Author | Blaser Software |
| License | Demo |
| Price | $999.00 |
| Released | 2016-03-26 |
| Downloads | 154 |
| Filesize | 492 kB |
| Requirements | Windows XP or better |
| Installation | No Install Support |
| Keywords | unlock, access, locked, workstation, user, desktop, admin, Administrator, machine, domain |
| Users' rating (15 rating) |
Using WinUnlock Free Download crack, warez, password, serial numbers, torrent, keygen, registration codes,
key generators is illegal and your business could subject you to lawsuits and leave your operating systems without patches.
We do not host any torrent files or links of WinUnlock on rapidshare.com, depositfiles.com, megaupload.com etc.
All WinUnlock download links are direct WinUnlock full download from publisher site or their selected mirrors.
Avoid: logged on user oem software, old version, warez, serial, torrent, WinUnlock keygen, crack.
Consider: WinUnlock full version, logged on user full download, premium download, licensed copy.