GIGABYTE USB Blocker B12.0921.1
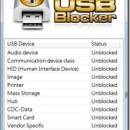
GIGABYTE USB Blocker is a useful application that is especially designed to provide you with a simple means of locking down USB ports on any system. With the help of this program you can prevent data leaks that may occur through USB devices. Using GIGABYTE USB Blocker is a breeze to operate, all you have to do is select the class of USB device that you want to disable, provide the password and that's all. ...
| Author | GIGABYTE TECHNOLOGY CO., LTD. |
| License | Freeware |
| Price | FREE |
| Released | 2012-10-20 |
| Downloads | 261 |
| Filesize | 9.20 MB |
| Requirements | |
| Installation | Instal And Uninstall |
| Keywords | USB blocker, port blocker, block USB device, block, port, disable |
| Users' rating (12 rating) |
Using GIGABYTE USB Blocker Free Download crack, warez, password, serial numbers, torrent, keygen, registration codes,
key generators is illegal and your business could subject you to lawsuits and leave your operating systems without patches.
We do not host any torrent files or links of GIGABYTE USB Blocker on rapidshare.com, depositfiles.com, megaupload.com etc.
All GIGABYTE USB Blocker download links are direct GIGABYTE USB Blocker full download from publisher site or their selected mirrors.
Avoid: risk 2 oem software, old version, warez, serial, torrent, GIGABYTE USB Blocker keygen, crack.
Consider: GIGABYTE USB Blocker full version, risk 2 full download, premium download, licensed copy.