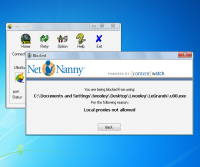
Net Nanny for Mac 2.0
Net Nanny is a powerful, yet simple to install parental control and internet safety solution that helps parents protect their children and monitor their Internet use. More than an Internet Filter, it is peace of mind. The latest installment of Net Nanny included some of the top customer requested features, especially around social networking, filter accuracy and circumvention. ...
| Author | ContentWatch |
| License | Trialware |
| Price | $39.99 |
| Released | 2010-03-31 |
| Downloads | 487 |
| Filesize | 1.00 MB |
| Requirements | |
| Installation | Instal And Uninstall |
| Keywords | filter, security, privacy, control, monitoring, child, kids, netnanny |
| Users' rating (44 rating) |
Using Net Nanny for Mac Free Download crack, warez, password, serial numbers, torrent, keygen, registration codes,
key generators is illegal and your business could subject you to lawsuits and leave your operating systems without patches.
We do not host any torrent files or links of Net Nanny for Mac on rapidshare.com, depositfiles.com, megaupload.com etc.
All Net Nanny for Mac download links are direct Net Nanny for Mac full download from publisher site or their selected mirrors.
Avoid: security monitoring oem software, old version, warez, serial, torrent, Net Nanny for Mac keygen, crack.
Consider: Net Nanny for Mac full version, security monitoring full download, premium download, licensed copy.