Stunnel 5.74
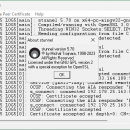
Stunnel, developed by Michal Trojnara, is a robust and versatile tool designed to add SSL encryption to existing network services without any changes to the programs' code. This open-source proxy encrypts data streams, ensuring secure communication over the internet. Ideal for securing legacy applications, Stunnel is highly configurable, supports a wide range of platforms, and is praised for its reliability and ease of use. ...
| Author | Michal Trojnara |
| License | Open Source |
| Price | FREE |
| Released | 2025-05-21 |
| Downloads | 618 |
| Filesize | 3.30 MB |
| Requirements | |
| Installation | Instal And Uninstall |
| Keywords | Stunnel, SSL encryption wrapper, remote server, remote client, encryption, wrapper, remote, SSL |
| Users' rating (18 rating) |
Using Stunnel Free Download crack, warez, password, serial numbers, torrent, keygen, registration codes,
key generators is illegal and your business could subject you to lawsuits and leave your operating systems without patches.
We do not host any torrent files or links of Stunnel on rapidshare.com, depositfiles.com, megaupload.com etc.
All Stunnel download links are direct Stunnel full download from publisher site or their selected mirrors.
Avoid: unauthorized access oem software, old version, warez, serial, torrent, Stunnel keygen, crack.
Consider: Stunnel full version, unauthorized access full download, premium download, licensed copy.