Romaco Timeout x64 3.1.4.0
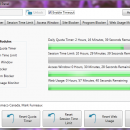
Romaco Timeout is a small and easy to use multi-user time-restriction tool designed to allow a user only so much time on their computer during the course of one day. If they go over this limit, they will be either logged off, or the computer shut down. They will only be able to log back in if the administration password is typed, or until the next day when the quota is reset. ...
| Author | Mark Furneaux |
| License | Freeware |
| Price | FREE |
| Released | 2013-05-23 |
| Downloads | 293 |
| Filesize | 2.44 MB |
| Requirements | Microsoft .NET Framework 4.0 |
| Installation | Instal And Uninstall |
| Keywords | Time restriction, Computer lockdown, Restrict usage, Restriction, Restrict, Lockdown |
| Users' rating (6 rating) |
Using Romaco Timeout x64 Free Download crack, warez, password, serial numbers, torrent, keygen, registration codes,
key generators is illegal and your business could subject you to lawsuits and leave your operating systems without patches.
We do not host any torrent files or links of Romaco Timeout x64 on rapidshare.com, depositfiles.com, megaupload.com etc.
All Romaco Timeout x64 download links are direct Romaco Timeout x64 full download from publisher site or their selected mirrors.
Avoid: usage oem software, old version, warez, serial, torrent, Romaco Timeout x64 keygen, crack.
Consider: Romaco Timeout x64 full version, usage full download, premium download, licensed copy.