Chop 1.9
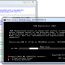
Using either a normal window, a wizard or command-line interface Chop will split large files (including ones larger than 4 GB) for easier distribution. Files can be split by either the number of files that you want, by file size, or you can use preset common sizes for floppies, CDs, USB drives, etc... Chop also supports corruption checking (detecting bit errors as well as translocation errors), UnChopping via BAT file and simple encryption. ...
| Author | Sinner Computing |
| License | Free To Try |
| Price | $10.00 |
| Released | 2022-09-29 |
| Downloads | 531 |
| Filesize | 44 kB |
| Requirements | |
| Installation | Install and Uninstall |
| Keywords | File, Split, Bat, assembly, security, Sinner, chop, wizard, CRC, Command line, bat |
| Users' rating (8 rating) |
Using Chop Free Download crack, warez, password, serial numbers, torrent, keygen, registration codes,
key generators is illegal and your business could subject you to lawsuits and leave your operating systems without patches.
We do not host any torrent files or links of Chop on rapidshare.com, depositfiles.com, megaupload.com etc.
All Chop download links are direct Chop full download from publisher site or their selected mirrors.
Avoid: access security oem software, old version, warez, serial, torrent, Chop keygen, crack.
Consider: Chop full version, access security full download, premium download, licensed copy.