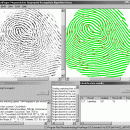
VeriFinger Algorithm Demo for MS Windows 6.5
Fingerprint recognition algorithm demo application enrolls and identifies fingers from supported scanners or image files. NIST MINEX-compliant technology. Fast matching (280,000 templates per second on Intel Core i7-2600) with reliability proven at FVC2006 and NIST FpVTE 2003. Translation, rotation and deformation tolerant enrollment with image quality determination and features generalization. Supports 90+ fingerprint reader models. ...
| Author | Neurotechnology |
| License | Demo |
| Price | $439.00 |
| Released | 2012-04-02 |
| Downloads | 276 |
| Filesize | 43.57 MB |
| Requirements | PC with 2GHz processor or better |
| Installation | Install and Uninstall |
| Keywords | fingerprint, recognition, identification, matching, verification, biometric, security, demo, application, roc |
| Users' rating (6 rating) |
Using VeriFinger Algorithm Demo for MS Windows Free Download crack, warez, password, serial numbers, torrent, keygen, registration codes,
key generators is illegal and your business could subject you to lawsuits and leave your operating systems without patches.
We do not host any torrent files or links of VeriFinger Algorithm Demo for MS Windows on rapidshare.com, depositfiles.com, megaupload.com etc.
All VeriFinger Algorithm Demo for MS Windows download links are direct VeriFinger Algorithm Demo for MS Windows full download from publisher site or their selected mirrors.
Avoid: algorithm 2 oem software, old version, warez, serial, torrent, VeriFinger Algorithm Demo for MS Windows keygen, crack.
Consider: VeriFinger Algorithm Demo for MS Windows full version, algorithm 2 full download, premium download, licensed copy.