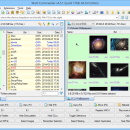
Multi Commander Portable 14.1.0.3017
Multi Commander portable has a everything you need in your daily works with files to make your work fast and efficient. It uses the very popular and efficient dual-panel layout. Multi Commander includes all the standard features of a file manager like copy, move, view, rename. But Multi Commander's big strength is the special features that allow you to do advanced task with ease. ...
| Author | Mathias Svensson |
| License | Freeware |
| Price | FREE |
| Released | 2024-06-24 |
| Downloads | 569 |
| Filesize | 10.50 MB |
| Requirements | |
| Installation | Instal And Uninstall |
| Keywords | file manager, multi-tab manager, folder management, manager, folder, commander, portable |
| Users' rating (87 rating) |
Using Multi Commander Portable Free Download crack, warez, password, serial numbers, torrent, keygen, registration codes,
key generators is illegal and your business could subject you to lawsuits and leave your operating systems without patches.
We do not host any torrent files or links of Multi Commander Portable on rapidshare.com, depositfiles.com, megaupload.com etc.
All Multi Commander Portable download links are direct Multi Commander Portable full download from publisher site or their selected mirrors.
Avoid: code security oem software, old version, warez, serial, torrent, Multi Commander Portable keygen, crack.
Consider: Multi Commander Portable full version, code security full download, premium download, licensed copy.