File Encryption XP 1.7.395
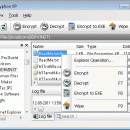
Need a military grade file encryption software? Would you like to delete (shred) files and be 100% sure they can't be "undeleted"? How about protecting data stored with removable drives? File Encryption XP does all that and more! File Encryption XP is password protection software for Windows. Files are encrypted with hack-proof Blowfish algorithm. This tool works with USB drives, flash memory cards, HDDs, ZIP drives, and works with any Windows PC ...
| Author | CP Lab |
| License | Free To Try |
| Price | $29.95 |
| Released | 2022-01-22 |
| Downloads | 2545 |
| Filesize | 1.66 MB |
| Requirements | Windows All, CPU P100, 16Mb RAM |
| Installation | Install and Uninstall |
| Keywords | encryption, encryption software, data encryption, security encryption, file encryption, file encryption software, encryption program, file encrypt, data encryption software, blowfish encryption, password protection |
| Users' rating (45 rating) |
Using File Encryption XP Free Download crack, warez, password, serial numbers, torrent, keygen, registration codes,
key generators is illegal and your business could subject you to lawsuits and leave your operating systems without patches.
We do not host any torrent files or links of File Encryption XP on rapidshare.com, depositfiles.com, megaupload.com etc.
All File Encryption XP download links are direct File Encryption XP full download from publisher site or their selected mirrors.
Avoid: computer use oem software, old version, warez, serial, torrent, File Encryption XP keygen, crack.
Consider: File Encryption XP full version, computer use full download, premium download, licensed copy.