ProxyCrypt 2.6.3
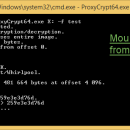
ProxyCrypt is a command line tool that creates encrypted volumes within a file or a hard drive. Designed for paranoids and advanced users, it is also fast, very lightweight, open source and easy to recompile. It works as a 'proxy' for the ImDisk driver, which is included in the full package. If you need to create encrypted spaces which can be partitioned like an ordinary hard drive, it is also compatible with Arsenal Image Mounter. ...
| Author | v77 |
| License | Freeware |
| Price | FREE |
| Released | 2022-03-06 |
| Downloads | 255 |
| Filesize | 467 kB |
| Requirements | - ImDisk or Arsenal Image Mounter - Administrative privileges - CPU with SSE2 |
| Installation | No Install Support |
| Keywords | volume, encryption, imdisk, command line |
| Users' rating (26 rating) |
Using ProxyCrypt Free Download crack, warez, password, serial numbers, torrent, keygen, registration codes,
key generators is illegal and your business could subject you to lawsuits and leave your operating systems without patches.
We do not host any torrent files or links of ProxyCrypt on rapidshare.com, depositfiles.com, megaupload.com etc.
All ProxyCrypt download links are direct ProxyCrypt full download from publisher site or their selected mirrors.
Avoid: disk read oem software, old version, warez, serial, torrent, ProxyCrypt keygen, crack.
Consider: ProxyCrypt full version, disk read full download, premium download, licensed copy.