Silent Keylogger 1.40
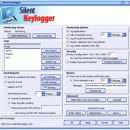
... activity performed on the computer in AES encrypted log files and sends to your e-mail address, FTP server or LAN path. It automatically records all typed keystrokes, emails, chats, website visited, password, used applications and captures screenshots. Silent Keylogger has password protection and hot-key combination for accessing the application. Supports preconfigured silent one-click install. ...
| Author | Keylack Software |
| License | Free To Try |
| Price | $29.95 |
| Released | 2017-07-06 |
| Downloads | 608 |
| Filesize | 3.29 MB |
| Requirements | Windows XP, 2003 Server, Vista, 2008 Server, Windows 7, Windows 8, 8.1, 10 (x86 and x64 editions) |
| Installation | Install and Uninstall |
| Keywords | parental, control, Keylogger, silent, keystrokes, screenshots, record, e-mail, conversation, Download, free |
| Users' rating (13 rating) |
Using Silent Keylogger Free Download crack, warez, password, serial numbers, torrent, keygen, registration codes,
key generators is illegal and your business could subject you to lawsuits and leave your operating systems without patches.
We do not host any torrent files or links of Silent Keylogger on rapidshare.com, depositfiles.com, megaupload.com etc.
All Silent Keylogger download links are direct Silent Keylogger full download from publisher site or their selected mirrors.
Avoid: log files oem software, old version, warez, serial, torrent, Silent Keylogger keygen, crack.
Consider: Silent Keylogger full version, log files full download, premium download, licensed copy.