How to Analyze Email Headers 1.3
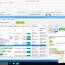
How to analyze email headers & How to collect email evidence was the biggest forensic query for all the forensic investigators who failed to succeed in many cyber forensic cases. Which were actually related to analyze forensic emails & to examine email header. It wasn’t possible for all the investigators to analyze forensic emails neither it was as easy as it is now. Email investigation of cyber forensics was always a tough job to do. ...
| Author | Analyze Forensic Emails |
| License | Free To Try |
| Price | $299.00 |
| Released | 2013-03-20 |
| Downloads | 165 |
| Filesize | 13.90 MB |
| Requirements | Pentium II 400 MHz, 64 MB RAM, Minimum 10 MB Space |
| Installation | Install and Uninstall |
| Keywords | How to analyze email headers, search email messages, how to collect email evidence, analyze forensic emails, email investigation, examine email header |
| Users' rating (27 rating) |
Using How to Analyze Email Headers Free Download crack, warez, password, serial numbers, torrent, keygen, registration codes,
key generators is illegal and your business could subject you to lawsuits and leave your operating systems without patches.
We do not host any torrent files or links of How to Analyze Email Headers on rapidshare.com, depositfiles.com, megaupload.com etc.
All How to Analyze Email Headers download links are direct How to Analyze Email Headers full download from publisher site or their selected mirrors.
Avoid: log on oem software, old version, warez, serial, torrent, How to Analyze Email Headers keygen, crack.
Consider: How to Analyze Email Headers full version, log on full download, premium download, licensed copy.