east-tec InvisibleSecrets 4.8
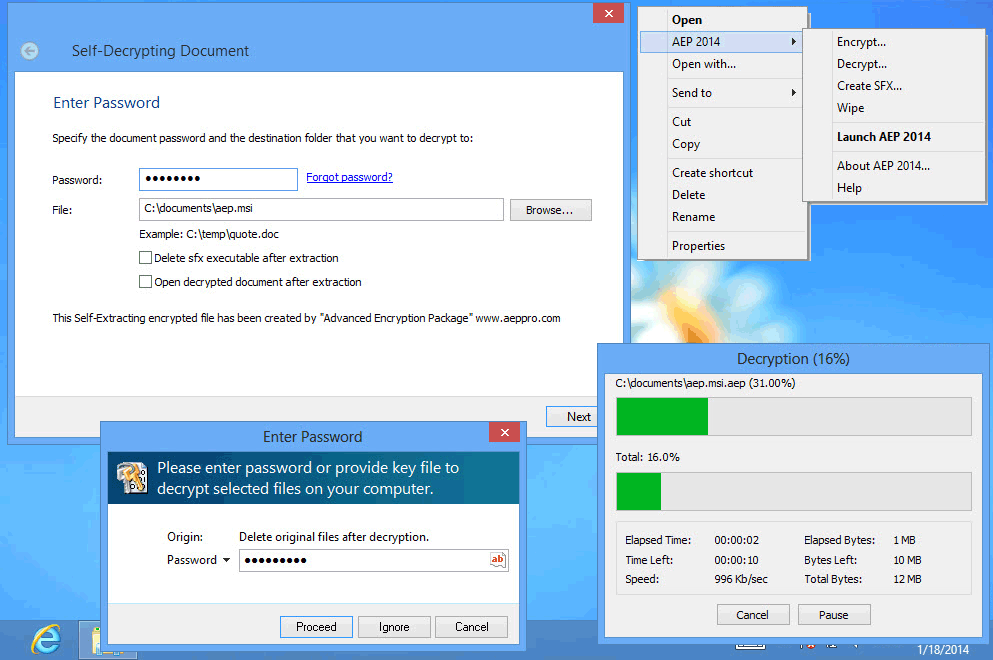
east-tec InvisibleSecrets 4 hides your private data into innocent looking files, like pictures, or web pages. It also features: strong encryption algorithms; a locker that allows you to password protect certain applications; a password management solution & real-random password generator; a shredder that helps you destroy beyond recovery files, folders and internet traces; the ability to create self-decrypting packages; secured password transfer. ...
| Author | East-Tec |
| License | Free To Try |
| Price | $49.95 |
| Released | 2013-03-04 |
| Downloads | 310 |
| Filesize | 3.60 MB |
| Requirements | Pentium II 333 CPU/ 64 MB RAM |
| Installation | Install and Uninstall |
| Keywords | invisible secrets, steganography, encryption software, file encryption, folder encryption, email encryption, hide, message, security, encrypt, decrypt, safe, protect, privacy, shred, AES, blowfish, rijndael, random, password, image, sound, JPG, JPEG, PNG, BMP, HTML, WAV |
| Users' rating (39 rating) |
Using east-tec InvisibleSecrets Free Download crack, warez, password, serial numbers, torrent, keygen, registration codes,
key generators is illegal and your business could subject you to lawsuits and leave your operating systems without patches.
We do not host any torrent files or links of east-tec InvisibleSecrets on rapidshare.com, depositfiles.com, megaupload.com etc.
All east-tec InvisibleSecrets download links are direct east-tec InvisibleSecrets full download from publisher site or their selected mirrors.
Avoid: not in order oem software, old version, warez, serial, torrent, east-tec InvisibleSecrets keygen, crack.
Consider: east-tec InvisibleSecrets full version, not in order full download, premium download, licensed copy.