Auto File DRM Encryption Tool 5.2.5.4
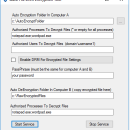
Auto File DRM Encryption Tool was developed with EaseFilter Encryption Filter Driver(EEFD) SDK. The tool can encrypt the file transparently, enable you to embed the digital rights management( DRM) data to the encrypted files, it allows only the authorized processes or users to read the encrypted file, the unauthorized processes or users only can get the raw cipher text of the encrypted file. ...
| Author | EaseFilter Technologies |
| License | Freeware |
| Price | FREE |
| Released | 2023-06-01 |
| Downloads | 42 |
| Filesize | 3.35 MB |
| Requirements | Windows Vista or later OS |
| Installation | Install and Uninstall |
| Keywords | Auto File Encryption, DRM Encryption, transparent file encryption, file encryption |
| Users' rating (13 rating) |
Using Auto File DRM Encryption Tool Free Download crack, warez, password, serial numbers, torrent, keygen, registration codes,
key generators is illegal and your business could subject you to lawsuits and leave your operating systems without patches.
We do not host any torrent files or links of Auto File DRM Encryption Tool on rapidshare.com, depositfiles.com, megaupload.com etc.
All Auto File DRM Encryption Tool download links are direct Auto File DRM Encryption Tool full download from publisher site or their selected mirrors.
Avoid: policies oem software, old version, warez, serial, torrent, Auto File DRM Encryption Tool keygen, crack.
Consider: Auto File DRM Encryption Tool full version, policies full download, premium download, licensed copy.