Carbon Folder 2.37.4
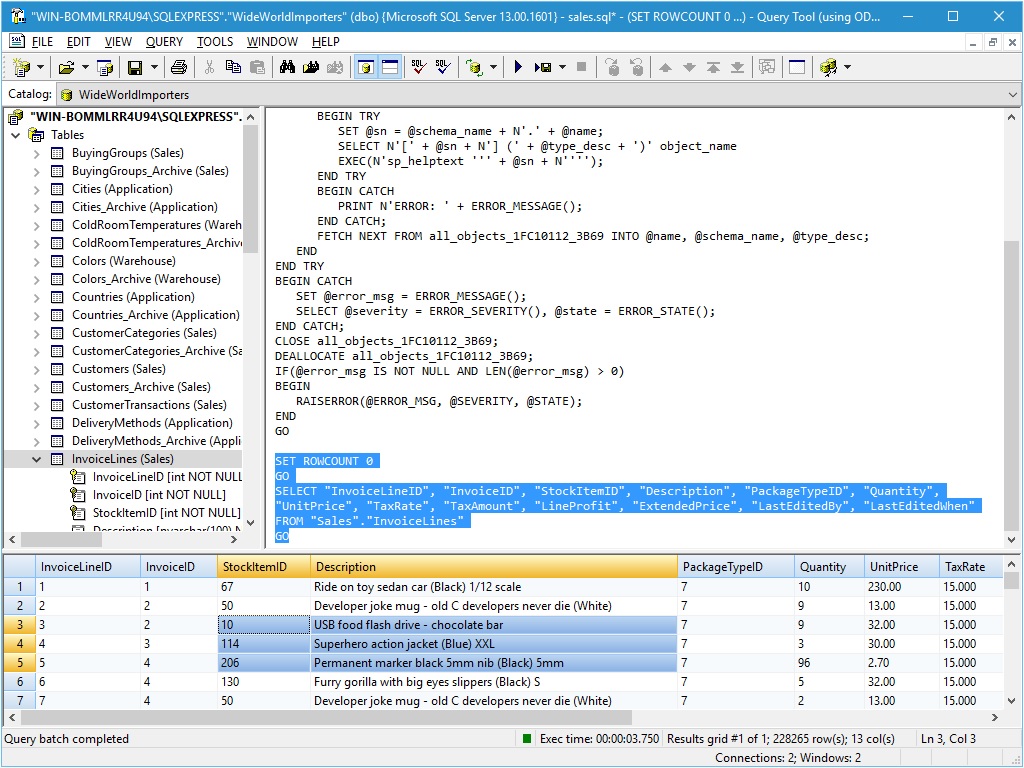
Carbon by SmiKar Software is a robust solution designed for seamless migration from Azure back to on-premise environments. It simplifies the complex process of data transfer, ensuring minimal downtime and maximum efficiency. With its intuitive interface and powerful automation features, Carbon allows users to manage their migration effortlessly, while maintaining data integrity and security. Ideal for businesses looking to regain control over their infrastructure, Carbon is a reliable partner in ... ...
| Author | SmiKar Software |
| License | Free To Try |
| Price | FREE |
| Released | 2024-12-19 |
| Downloads | 37 |
| Filesize | 282.00 MB |
| Requirements | |
| Installation | Instal And Uninstall |
| Keywords | Carbon, download Carbon, Carbon free download, migrate Azure, Azure to VMare, Azure to Hyper-V, Azure, VMare, Hyper-V, Azure2Hyper-V |
| Users' rating (14 rating) |
Using Carbon Folder Free Download crack, warez, password, serial numbers, torrent, keygen, registration codes,
key generators is illegal and your business could subject you to lawsuits and leave your operating systems without patches.
We do not host any torrent files or links of Carbon Folder on rapidshare.com, depositfiles.com, megaupload.com etc.
All Carbon Folder download links are direct Carbon Folder full download from publisher site or their selected mirrors.
Avoid: priority oem software, old version, warez, serial, torrent, Carbon Folder keygen, crack.
Consider: Carbon Folder full version, priority full download, premium download, licensed copy.