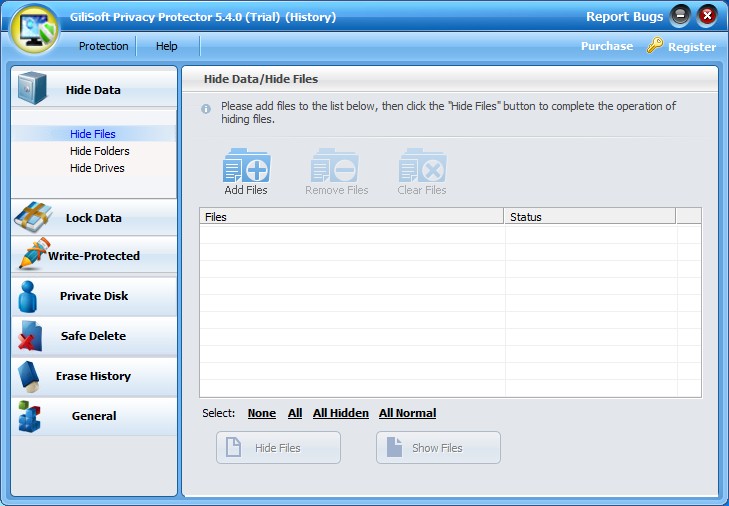
DirCryptHide 1.58
Any number of folders with all subfolders (even on different drives) can be moved in a highly scripted Container file (created with TrueCrypt). This can be opened with password/USB-Device if needed. In this state you can work normal with the stored data, En/decryption is performed "on-the-fly", the data in the container will always be encrypted. ...
| Author | Gunnar Daehling |
| License | Freeware |
| Price | FREE |
| Released | 2011-03-11 |
| Downloads | 547 |
| Filesize | 3.15 MB |
| Requirements | Standard |
| Installation | Install and Uninstall |
| Keywords | Encryption, truecrypt, on the fly, hide folder, safe, tresor, container, hide, ordner, password, invisible, protect |
| Users' rating (14 rating) |
|
| Our rating |

|
Using DirCryptHide Free Download crack, warez, password, serial numbers, torrent, keygen, registration codes,
key generators is illegal and your business could subject you to lawsuits and leave your operating systems without patches.
We do not host any torrent files or links of DirCryptHide on rapidshare.com, depositfiles.com, megaupload.com etc.
All DirCryptHide download links are direct DirCryptHide full download from publisher site or their selected mirrors.
Avoid: program protection oem software, old version, warez, serial, torrent, DirCryptHide keygen, crack.
Consider: DirCryptHide full version, program protection full download, premium download, licensed copy.