4n6 OLM Forensics Tool 3.0
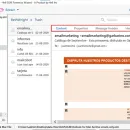
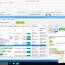
4n6 OLM Forensics Tool for Investigators helps perform analysis on OLM File data: Mail, Calendar, Contacts, Tasks & Notes. The software provides 5 Modes to Analyze Mac OLM files in: Content, Properties, Message Header, Hex View & Raw Message. It is capable Examine & acquire OLM message with attachments & complete header details in more than 10+ file formats & web based servers. ...
| Author | 4n6 OLM Forensics |
| License | Free To Try |
| Price | $49.00 |
| Released | 2023-11-23 |
| Downloads | 80 |
| Filesize | 43.85 MB |
| Requirements | 1 GHz Processor, 512 MB RAM, Minimum 100 MB Space |
| Installation | Install and Uninstall |
| Keywords | olm forensics tool, olm file forensics, olm forensic software, olm forensics utility |
| Users' rating (37 rating) |
Using 4n6 OLM Forensics Tool Free Download crack, warez, password, serial numbers, torrent, keygen, registration codes,
key generators is illegal and your business could subject you to lawsuits and leave your operating systems without patches.
We do not host any torrent files or links of 4n6 OLM Forensics Tool on rapidshare.com, depositfiles.com, megaupload.com etc.
All 4n6 OLM Forensics Tool download links are direct 4n6 OLM Forensics Tool full download from publisher site or their selected mirrors.
Avoid: retrieve information oem software, old version, warez, serial, torrent, 4n6 OLM Forensics Tool keygen, crack.
Consider: 4n6 OLM Forensics Tool full version, retrieve information full download, premium download, licensed copy.