Super Rolodex 6.0
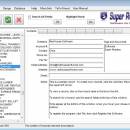
SuperRolodex is simple and very straight forward to use, and its capability to become whatever data retrieving tool you want it to be is what makes SuperRolodex so powerful. All your records can be found using keyword searches. You can even create custom electonic catalogs with the built-in file linking feature. This program will make your life at home and at work much more easy, efficient and productive. ...
| Author | Red House Software |
| License | Free To Try |
| Price | $37.95 |
| Released | 2015-06-07 |
| Downloads | 115 |
| Filesize | 3.67 MB |
| Requirements | Windows 95 and above |
| Installation | Install and Uninstall |
| Keywords | rolodex, database management software, crm software, dbms software, database design, diy database, easy database |
| Users' rating (7 rating) |
Using Super Rolodex Free Download crack, warez, password, serial numbers, torrent, keygen, registration codes,
key generators is illegal and your business could subject you to lawsuits and leave your operating systems without patches.
We do not host any torrent files or links of Super Rolodex on rapidshare.com, depositfiles.com, megaupload.com etc.
All Super Rolodex download links are direct Super Rolodex full download from publisher site or their selected mirrors.
Avoid: top e oem software, old version, warez, serial, torrent, Super Rolodex keygen, crack.
Consider: Super Rolodex full version, top e full download, premium download, licensed copy.